Introduction
Within This Page
All facilities face a certain level of risk associated with various threats. These threats may be the result of natural events, accidents, or intentional acts to cause harm. Regardless of the nature of the threat, facility owners have a responsibility to limit or manage risks from these threats to the extent possible. The federal government has implemented The Risk Management Process for Federal Facilities: An Interagency Security Committee Standard which states,
"Risk is a function of the values of threat, consequence, and vulnerability. The objective of risk management is to create a level of protection that mitigates vulnerabilities to threats and the potential consequences, thereby reducing risk to an acceptable level. A variety of mathematical models are available to calculate risk and to illustrate the impact of increasing protective measures on the risk equation."
Facility owners, particularly owners of public facilities, should develop and implement a security risk management methodology which adheres to the Interagency Security Committee (ISC) standard while also supporting the security needs of the organization. Landlords who desire to lease space to federal government agencies should implement the ISC standard in the design of new facilities and/or the renovation of existing facilities.
Description
A. Threat Assessment

Figure 1. The tornado damaged Cash America Building in Fort Worth, TX
The first step in a risk management program is a threat assessment. A threat assessment considers the full spectrum of threats (i.e., natural, criminal, terrorist, accidental, etc.) for a given facility/location. The ISC standard only addresses man-made threats, but individual agencies are free to expand upon the threats they consider. The assessment should examine supporting information to evaluate the relative likelihood of occurrence for each threat. For natural threats, historical data concerning frequency of occurrence for given natural disasters such as tornadoes, hurricanes, floods, fire, or earthquakes can be used to determine the credibility of the given threat. For criminal threats, the crime rates in the surrounding area provide a good indicator of the type of criminal activity that may threaten the facility. In addition, the type of assets and/or activity located in the facility may also increase the target attractiveness in the eyes of the aggressor. The type of assets and/or activity located in the facility will also relate directly to the likelihood of various types of accidents. For example, a facility that utilizes heavy industrial machinery will be at higher risk for serious or life-threatening job related accidents than a typical office building.
For terrorist threats, the attractiveness of the facility as a target is a primary consideration. In addition, the type of terrorist act may vary based on the potential adversary and the method of attack most likely to be successful for a given scenario. For example, a terrorist wishing to strike against the federal government may be more likely to attack a large federal building than to attack a multi-tenant office building containing a large number of commercial tenants and a few government tenants. However, if security at the large federal building makes mounting a successful attack too difficult, the terrorist may be diverted to a nearby facility that may not be as attractive from an occupancy perspective, but has a higher probability of success due to the absence of adequate security. In general, the likelihood of terrorist attacks cannot be quantified statistically since terrorism is, by its very nature random. Specific definitions are important to quantify the level of each threat. The more specific the definition, the more consistent the assessments will be especially if the assessments are being performed by a large number of assessors. Example assessments are provided below:
-
Defined: Man-made: There are aggressors who utilize this tactic who are known to be targeting this facility or the organization. There is a history of this type of activity in the area and this facility is a known target. Specific threats have been received or identified by law enforcement agencies. Natural: Events of this nature occur in the immediate vicinity on a frequent basis.
-
Credible: Man-made: There are aggressors who utilize this tactic who are known to target this type of facility. There is a history of this type of activity in the area and this facility and/or similar facilities have been targets previously. No specific threat has been received or identified by law enforcement agencies. Natural: Events of this nature occur in the immediate vicinity periodically (i.e. once every 10 years).
-
Potential:Man-made: There are aggressors who utilize this tactic, but they are not known to target this type of facility. There is a history of this type of activity in the area, but this facility has not been a target. Natural: Events of this nature occur in the region on a sporadic basis.
-
Minimal: Man-made: No aggressors who utilize this tactic are identified for this facility and there is no history of this type of activity at the facility or the neighboring area. Natural: There is no history of this type of event in the area.
B. Vulnerability Assessment
Once the plausible threats are identified, a vulnerability assessment must be performed. The vulnerability assessment considers the potential impact of loss from a successful attack as well as the vulnerability of the facility/location to an attack. Impact of loss is the degree to which the mission of the agency is impaired by a successful attack from the given threat. A key component of the vulnerability assessment is properly defining the ratings for impact of loss and vulnerability. These definitions may vary greatly from facility to facility. For example, the amount of time that mission capability is impaired is an important part of impact of loss. If the facility being assessed is an Air Route Traffic Control Tower, a downtime of a few minutes may be a serious impact of loss, while for a Social Security office a downtime of a few minutes would be minor. A sample set of definitions for impact of loss is provided below. These definitions are for an organization that generates revenue by serving the public.
-
Devastating: The facility is damaged/contaminated beyond habitable use. Most items/assets are lost, destroyed, or damaged beyond repair/restoration. The number of visitors to other facilities in the organization may be reduced by up to 75% for a limited period of time.
-
Severe: The facility is partially damaged/contaminated. Examples include partial structure breach resulting in weather/water, smoke, impact, or fire damage to some areas. Some items/assets in the facility are damaged beyond repair, but the facility remains mostly intact. The entire facility may be closed for a period of up to two weeks and a portion of the facility may be closed for an extended period of time (more than one month). Some assets may need to be moved to remote locations to protect them from environmental damage. The number of visitors to this and other facilities in the organization may be reduced by up to 50% for a limited period of time.
-
Noticeable: The facility is temporarily closed or unable to operate, but can continue without an interruption of more than one day. A limited number of assets may be damaged, but the majority of the facility is not affected. The number of visitors to this and other facilities in the organization may be reduced by up to 25% for a limited period of time.
-
Minor: The facility experiences no significant impact on operations (downtime is less than four hours) and there is no loss of major assets.
Vulnerability is defined to be a combination of the attractiveness of a facility as a target and the level of deterrence and/or defense provided by the existing countermeasures. Target attractiveness is a measure of the asset or facility in the eyes of an aggressor and is influenced by the function and/or symbolic importance of the facility. Sample definitions for vulnerability ratings are as follows:
-
Very High: This is a high profile facility that provides a very attractive target for potential adversaries, and the level of deterrence and/or defense provided by the existing countermeasures is inadequate.
-
High: This is a high profile regional facility or a moderate profile national facility that provides an attractive target and/or the level of deterrence and/or defense provided by the existing countermeasures is inadequate.
-
Moderate: This is a moderate profile facility (not well known outside the local area or region) that provides a potential target and/or the level of deterrence and/or defense provided by the existing countermeasures is marginally adequate.
-
Low: This is not a high profile facility and provides a possible target and/or the level of deterrence and/or defense provided by the existing countermeasures is adequate.
The vulnerability assessment may also include detailed analysis of the potential impact of loss from an explosive, chemical or biological attack. Professionals with specific training and experience in these areas are required to perform these detailed analyses. A sample of the type of output that can be generated by a detailed explosive analysis is shown in Figure 2. This graphic representation of the potential damage to a facility from an explosive attack allows a building owner to quickly interpret the results of the analysis. In addition, similar representations can be used to depict the response of an upgraded facility to the same explosive threat. This allows a building owner to interpret the potential benefit that can be achieved by implementing various structural upgrades to the building frame, wall, roof and/or windows. The results of blast assessment depicted in Figure 2 were for glazing only.
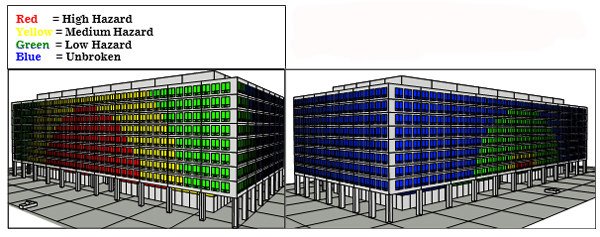
Figure 2. Existing facility (left) and upgraded facility (right)
C. Risk Analysis
A combination of the impact of loss rating and the vulnerability rating can be used to evaluate the potential risk to the facility from a given threat. A sample risk matrix is depicted in Table 1. High risks are designated by the red cells, moderate risks by the yellow cells, and low risks by the green cells.
Table 1. Matrix identifying levels of risk
| Minimal Threat | ||||
|---|---|---|---|---|
| Vulnerability | ||||
| Impact of Loss | Low | Medium | High | Very High |
| Minor | ||||
| Noticeable | ||||
| Severe | ||||
| Devastating | ||||
| Potential Threat | ||||
| Vulnerability | ||||
| Impact of Loss | Low | Medium | High | Very High |
| Minor | ||||
| Noticeable | ||||
| Severe | ||||
| Devastating | ||||
| Credible Threat | ||||
| Vulnerability | ||||
| Impact of Loss | Low | Medium | High | Very High |
| Minor | ||||
| Noticeable | ||||
| Severe | ||||
| Devastating | ||||
| Defined Threat | ||||
| Vulnerability | ||||
| Impact of Loss | Low | Medium | High | Very High |
| Minor | ||||
| Noticeable | ||||
| Severe | ||||
| Devastating | ||||
The ratings in the matrix can be interpreted using the explanation shown in Table 2.
Table 2. Interpretation of the risk ratings
| Rating Category | Description |
|---|---|
| Very High | The risk is totally unacceptable. Immediate measures must be taken to reduce these risks and mitigate hazards. |
| High | The risk is unacceptable. Measures to reduce risk and mitigation hazards should be implemented as soon as possible. |
| Medium | The risk may be acceptable over the short term. Plans to reduce risk and mitigate hazards should be included in future plans and budgets. |
| Low | The risks are acceptable. Measures to further reduce risk or mitigate hazards should be implemented in conjunction with other security and mitigation upgrades. |
D. Upgrade Recommendations
Based on the findings from the risk analysis, the next step in the process is to identify countermeasure upgrades that will lower the various levels of risk. If an organization has minimum standard countermeasures for a given facility level which are not currently present, these countermeasures should automatically be included in the upgrade recommendations. Additional countermeasure upgrades above the organization's recommended minimum standards should be recommended as necessary to address the specific threats and associated unacceptable risks identified for the facility. The estimated capital cost of implementing the recommended countermeasures is usually provided. The estimated installation and operating costs for the recommended countermeasures are also usually provided. All operating costs are customarily estimated on a per year basis.


Figure 3. These photos depict two windows subjected to a large explosion. The unprotected window on the left fails catastrophically. The protected window on the right retains glass fragments and poses a significantly lower hazard to occupants.
E. Re-Evaluation of Risks
The implementation of the recommended security and/or structural upgrades should have a positive effect on the impact of loss and/or the vulnerability ratings for each threat. The final step in the process is to re-evaluate these two ratings for each threat in light of the recommended upgrades. Using an exterior explosive threat as an example, the installation of window retrofits (i.e., security window film, laminated glass, etc.) will not prevent the explosive attack from occurring, but it should reduce the impact of loss/injury caused by hazardous flying glass. Therefore, the impact of loss rating for an explosive threat would improve, but the vulnerability rating would stay the same. A second example could be introduction of an explosive into the interior of the facility. The potential upgrade for this threat might be X-ray package screening for every package entering the facility. While the potential impact of loss from an internal detonation remains the same, the vulnerability to an attack is lessened because a package containing explosives should be detected prior to entering the facility. To further reduce risk, structural hardening of the package screening areas could also reduce potential impact of loss. Reduction of either the impact of loss rating or the vulnerability rating has a positive effect on the reduction of overall risk.
F. Summary
The overall threat/vulnerability and risk analysis methodology is summarized by the following flowchart.
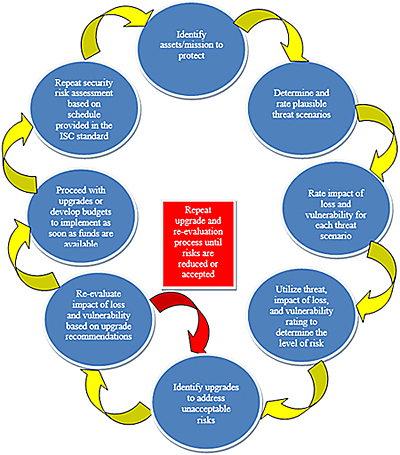
Figure 4. Flowchart depicting the basic risk assessment process
Application
Threat/vulnerability assessments and risk analysis can be applied to any facility and/or organization. The federal government has been utilizing varying types of assessments and analyses for many years. Federal Security Risk Management (FSRM) is basically the process described in this paper. FSRM is currently being used by several federal agencies as well as commercial businesses to assess their facilities.
Software is available to assist in performing threat/vulnerability assessments and risk analyses. The software tool associated with implementation of FSRM is entitled FSR-Manager. This tool is designed to be used by security personnel and allows the user to:
- Input a description of the facility, including number of people occupying the facility, the tenants represented, the contacts made during the assessment, any information gathered from the contacts, the construction details, etc.
- Input existing countermeasures.
- Input threats and rate.
- Assign an impact of loss to each threat.
- Input countermeasure upgrade alternatives and their associated costs.
FSR-Manager uses the above inputs to:
- Calculate vulnerability to each threat based on existing countermeasures.
- Determine the risk level from each threat and classify the risk level as high, medium, or low.
- Check the existing countermeasures against a list of ISC recommended countermeasures for the given facility security level and specific threats. The user is provided a list of potential countermeasure upgrades from which the user may choose what to recommend for implementation.
- Re-evaluate the vulnerability and associated risk level for each threat based on countermeasure upgrade recommendations.
- Use all of the input information to complete a template report in Microsoft Word.
More information about FSR-Manager can be found at www.ara.com.
Relevant Codes and Standards
- Executive Order 12977, "Interagency Security Committee"
- Federal Emergency Management Agency (FEMA)
- Interagency Security Committee (ISC) Security Design Criteria—Defines Threat/Risk classifications and resultant federal protective design requirements (Official Use Only)
- Unified Facilities Criteria (UFC)—UFC 4-010-01 DoD Minimum Anti-Terrorism Standards for Buildings—Establishes prescriptive procedures for Threat, Vulnerability and Risk assessments and security design criteria for DoD facilities (Official Use Only)
Additional Resources
Federal Agencies
- Federal Emergency Management Agency (FEMA) Terrorist Hazards Preparedness
- Federal Protective Service (FPS)—managed by the Department of Homeland Security, this federal law enforcement agency provides integrated security and law enforcement services to federally owned and leased buildings, facilities, properties and other assets
Design and Analysis Tools
- FSR-Manager—Proprietary software developed by Applied Research Associates, Inc. (ARA) to assist in performing threat/vulnerability assessments and risk analyses
- RAMPART™ (Risk Assessment Method—Property Analysis and Ranking Tool)—Developed by Sandia National Laboratories as a screening-level software program to determine the risk to a building by natural hazards, crime, and terrorism
Organizations and Associations
- American Society of Industrial Security (ASIS)—A leading non-profit association of security managers, product manufacturers, and consultants offering a variety of publications and programs including Threat and Vulnerability Assessment training
- International Association of Professional Security Consultants (IAPSC)—An association of security consultants whose members frequently perform Vulnerability Assessments
Publications
- Are Your Tenants Safe? BOMA's Guide to Security and Emergency Planning by Building Owners and Managers Association. Provides a template and instructions for completing a Threat, Vulnerability and Risk Assessment on commercial and institutional properties.
- BIPS 05 Preventing Structures from Collapsing by Department of Homeland Security (DHS), 2011.
- Multi-hazard Identification and Risk Assessment (MHIRA) by Federal Emergency Management Agency (FEMA).








